Overview
While working on this lab, its highly recommended that you keep open the following files/terminals to help with reference and debugging:
-
Code editor with
sr_router.c,sr_protocol.h -
Terminal
sshed to the VM, and execute./run_mininet.sh -
Open up a terminal at the client and two terminals at the router using
xterm clientandxterm sw0(twice). -
Function Reference List on your web browser
sr_handlepacket
The function of sr_handlepacket is to parse the Ethernet header and hand the packet stripped of the Ethernet header to handle_ip or handle_arp. This function is sr_handlepacket. The figure below illustrates this.
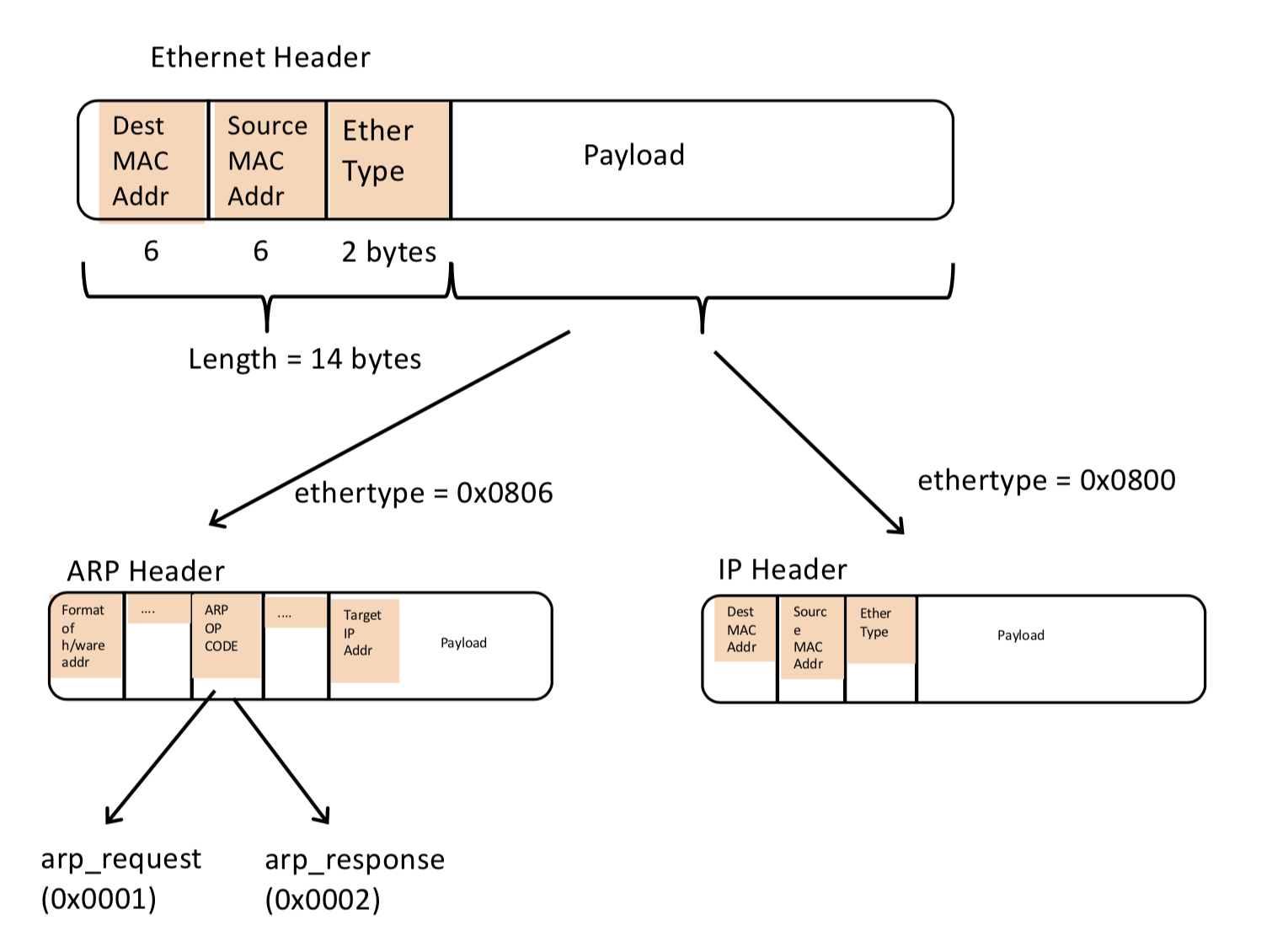
-
sr_handlepackettakes as input:-
struct sr_instance * sr: an instance of the router -
uint8_t packet: the packet with the ethernet header -
unsigned int len: the length of the packet -
char * interface: and the router’s interface name (eth0,eth1,eth2)
-
-
Read the comments for the first function call
sr_get_interface. Take a look at the Function Reference List. Note thatsr_get_interface:-
takes as input: the router instance, and a valid interface to this router at (
eth0,eth1,eth2). -
returns: an interface of type
struct sr_iffor the router, -
The fields of
struct sr_ifinclude an IP and MAC address of the router.
-
ToDos in sr_handlepacket
-
Step 1: call
ether_to_meto check if the packet is destined to this router. Inputs toether_to_me:-
Router’s MAC address: This is returned as a field in
sr_get_interface -
Destination MAC address of the packet: In the packet’s ethernet header. We can access the ethernet header by creating a struct pointer similar to Labs 5 and 6. Something like:
//defined in sr_protocol.h struct sr_ethernet_hdr * ehdr = (struct sr_ethernet_hdr *) packet; ehdr -> ether_dhost //gives us the destination ethernet header of the packet.
-
If
ether_to_medoes not return 1, then justreturnat this point. Else, we check if the packet has a valid length.
-
-
The packet should atleast be as big as the ethernet header for it to be valid. So a check would look like the following:
if(len < sizeof(struct sr_ethernet_hdr)){ return; } -
Once both checks pass, we can now parse the packet depending on
ether_typefield of thestruct sr_ethernet_hdr. Lines 192-195 ofsr_protocol.hspecify theether_typesyou should process. Note these macros are defined in host-byte order while the packet’sether_typefield is in network-byte order! To compare the packet’sether_typewith IP or ARP you could write:if (ehdr->ether_type == htons(ethertype_arp))..else...IP
-
Depending on whether it is an IP or ARP packet your code should strip the ethernet header and pass off the packet to either
handle_iporhandle_arp. For e.g., passing it tohandle_arp, we would need to change bothpacketandlento accommodate the packet without the ethernet header. You can use pointer arithmetic to pass the packet without the ethernet header, aspacket + sizeof(struct sr_ethernet_hdr)or asehdr + 1. Thelenwould need to be decremented bysizeof(struct sr_ethernet_hdr). -
You are now ready to start on
handle_arp! Note that this time, we want a pointer to the packet header of typestruct sr_arp_hdr(also defined insr_protocol.h) since our packet now starts at the ARP header.
Testing
Once you have written the case for arp_op_request in handle_arp you can check if your ARP responses work using Wireshark. To setup wireshark you would need the following:
-
At the router terminal
xterm sw0, start wireshark. Ignore the warning message that pops up. In wireshark start monitoring packets onsw0- (eth0,eth1,eth2). -
Open a different router terminal and
cd routerand runmakeand run your router code./sr. -
Open up a client terminal
xterm client, and issue a HTTP request to one of the servers:wget 192.168.2.2. -
Now, you should be able to see the ARP request in Wireshark that the client issued to the router, and if your code is correct, you should be returning an ARP response. You should also see subsequent TCP packets trying to flow through the router and failing (since we haven’t implemented forwarding yet). You can now stop wireshark and continue to write up your code for the router.
At any point if you would like to debug your code, you can run sr_solution to see what a working solution would look like and inspect the fields for the various protocol headers in wireshark.